Filter by

Blog
|
4 Min Read
Why Software Management is Critical to Your Cybersecurity
Software asset management (SAM) is an integral component of every organization’s cybersecurity efforts. Every piece of s...
Read More
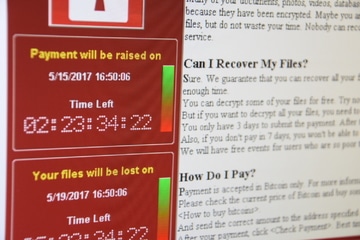
Blog
|
4 min read
Taking Down Your Business
What would happen if you had a multi-location hospitality business and had to close multiple locations? If a possible da...
Read More

Blog
|
4 Min Read
3 Key Reasons Why It's Important to Perform Recurring System Clean Up
Keeping your computer systems functioning and operational is essential for the success of every business or organization...
Read More

Blog
|
4 Min Read
Top 5 Benefits Of An Electronic Signature Solution
Still relying on plain old pen and paper for your legal documentation and signatures? Learn about 5 key features of elec...
Read More

Blog
|
5 Min Read
What to Consider Before Spending Money on Security Compliance
Here are five questions you should ask yourself before spending a significant portion of your organization’s budget on s...
Read More

Blog
|
4 Min Read
3 Reasons Why You Should Restrict User Permissions
You likely wouldn’t hand the keys to your home over to a stranger — so why would you consider that with your business by...
Read More
