
Managed Security Services
Need essential best practices deployed to protect your organization and meet cyber insurance and compliance requirements? VC3 includes foundational cybersecurity tools and solutions as part of our managed services.
If that’s not enough, we also provide powerful add-ons to address additional risks and specific needs.
Organizations turn to VC3 for
Managed Security Services when they...
Understanding the Cybersecurity Landscape
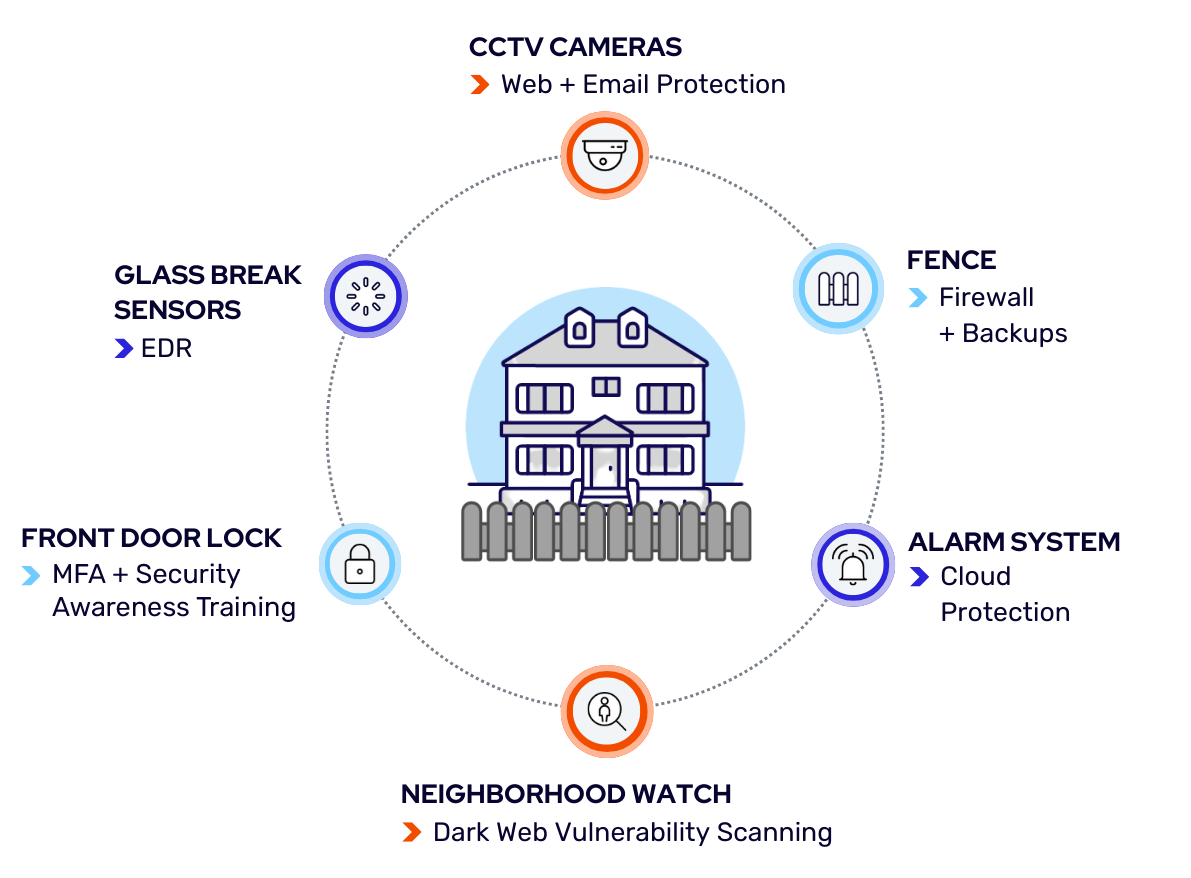
Managed Security Options
Powerful Cybersecurity. Simplified.
VC3 Managed Services
Our core managed services offerings—VC3 Manage, VC3 Manage Essentials, and VC3 Co-Manage—now include foundational cybersecurity protection as standard. When we manage your IT environment, we ensure that 7 essential baseline items are provided.
Endpoint Detection and Response (EDR)
Detect suspicious behavior and potential cyberattacks on endpoint devices like servers, desktops, and laptops, before cyber attackers can strike.
Cloud Protection
24/7/365 protection of your SaaS applications like Microsoft 365 or Google Workspace.
Phishing Tests + Security Awareness Training
Help keep employees sharp, skilled, and smart to counter cyberattackers.
Dark Web Credential Monitoring
Get real-time alerts when your information is found on the dark web so you can take proactive action against identity theft, blackmail, and more.
Email Protection
Encrypt your email, scan it for malware, and stop most phishing and spam attempts from ever reaching your employees.
Web Content Filtering
Proactively blocks employees from accessing malicious or risky websites.
Microsoft 365 MFA (P1 License Required)
Protect user account access for Microsoft 365 files and data.
For organizations that require additional security, we provide the following cybersecurity tools and solutions as add-ons.
SIEM/SOAR
Prioritize alerts and automate your response to common cybersecurity threats in complex IT environments.
For organizations that:
- Need fast threat detection despite receiving alerts from multiple tools.
- Need automated responses to common threats so that human error is mitigated.
- Require detailed reporting and monitoring of security events to comply with regulations.
Device MFA
Confirm that every user and their device are trusted before allowing access to your network.
For organizations that:
- Have a heightened risk of compromised devices.
- Need to apply MFA across more than just Microsoft 365 applications.
- Require higher security beyond user verification, especially in industries with strict compliance.
Vulnerability Management
Continuously identify and mitigate the highest risks in your IT environment.
For organizations that:
- Need help identifying, prioritizing, and fixing security weaknesses in a complex IT environment.
- Struggle with manually addressing vulnerabilities due to resource constraints.
- Require detailed vulnerability reporting and monitoring to satisfy compliance regulations.
For organizations that:
- Lack in-house compliance expertise.
- Have a high risk of compliance violations and fines.
- Struggle with compliance documentation, reporting, and audit readiness.
For organizations that:
- Struggle with managing multiple complex passwords.
- Have compliance requirements that mandate strong password policies and detailed audit trails.
- Need a secure, centralized solution to manage passwords and reduce unauthorized access risks.
What Our Clients Are Saying
We hadn’t seen anyone like VC3 before.
I was pleasantly surprised by VC3’s remote IT support and how well it served our city. We learned the hard way that we needed a vendor that helped us stay secure from ransomware and cyberattacks, update and patch everything constantly, and stay on top of IT issues. With VC3, everything is getting done. You don’t know what you’re missing if you’ve never seen it before—and we hadn’t seen anyone like VC3 before.

Great working relationship.
We have such a great working relationship and we’re always talking about the next thing. Chris and VC3 are my trusted advisors.
.jpg?width=70&height=70&name=StolleryLogo%20(RGB).jpg)
They placed us in a position to better service our staff.
When it comes to establishing an effective IT infrastructure, consulting experienced professionals is the first and most important step. It is one we are glad to have taken with VC3 as they placed us in a position to better service our staff and the residents of our city.

VC3 has so far been the most enjoyable.
I've been working with outsourcing partners since 1998 and working with VC3 has so far been the most enjoyable and least painful experience.

Our Strategic Advisor has always been a fantastic advocate for us.
Our Strategic Advisor has always been a fantastic advocate for us. If we do have issues, he’s a reasonable voice that is very good at seeing our perspective and helping us see it through.

VC3 gets IT out of sight, out of mind, and out of your way.
Response Time + Onsite Support
From a Team of 100% North American-Based Experts
of Experience Evolving with the Threat Landscape
Average Relationship Tenure
Our approach to technology enables your organization to AIM Higher.
Lots of companies can set up your laptops or manage your infrastructure. In order to contend with today's challenges, you need more than a break-fix vendor with a "24/7" help desk ticket to nowhere. You need a proactive partner that stops the issues before they start. That's where VC3 comes in.
Flexible and Comprehensive
Managed Security Solutions
| Included with VC3 Managed Services (Manage, Essentials, and Co-Manage) |
Additional Cybersecurity Services |
| EDR | SIEM/SOAR |
| Cloud Protection | Device MFA |
|
Phishing Tests and Security Awareness Training |
Vulnerability Management |
| Dark Web Protection | Compliance as a Service |
| Email Protection | Password Management |
| Web Content Filtering | |
|
Microsoft 365 MFA (P1 License Required) |
Let's talk about how VC3 can help you AIM higher.
Cybersecurity Resources + Insights

How Much Do Managed Cybersecurity Services Cost?

Top 10 Tips for Choosing an Outsourced Cyber Security Company
