
CMMC Compliance Consulting, Gap Analysis & Audit Readiness Assessment Services
Be ready to pass your CMMC audit and secure more contracts.
Confidently obtain—and retain—contracts with the DoD.
Prove You're Secure
For better or worse, compliance with CMMC is not optional for those in the DoD supply chain. The new certification is part of a continual effort to provide more accurate results, provide more helpful insights, and reveal the best practice for DoD operations.
Keeping and gaining more DoD contracts depends on your ability to verify that you can achieve and maintain the level of security that is required through your DoD contract.
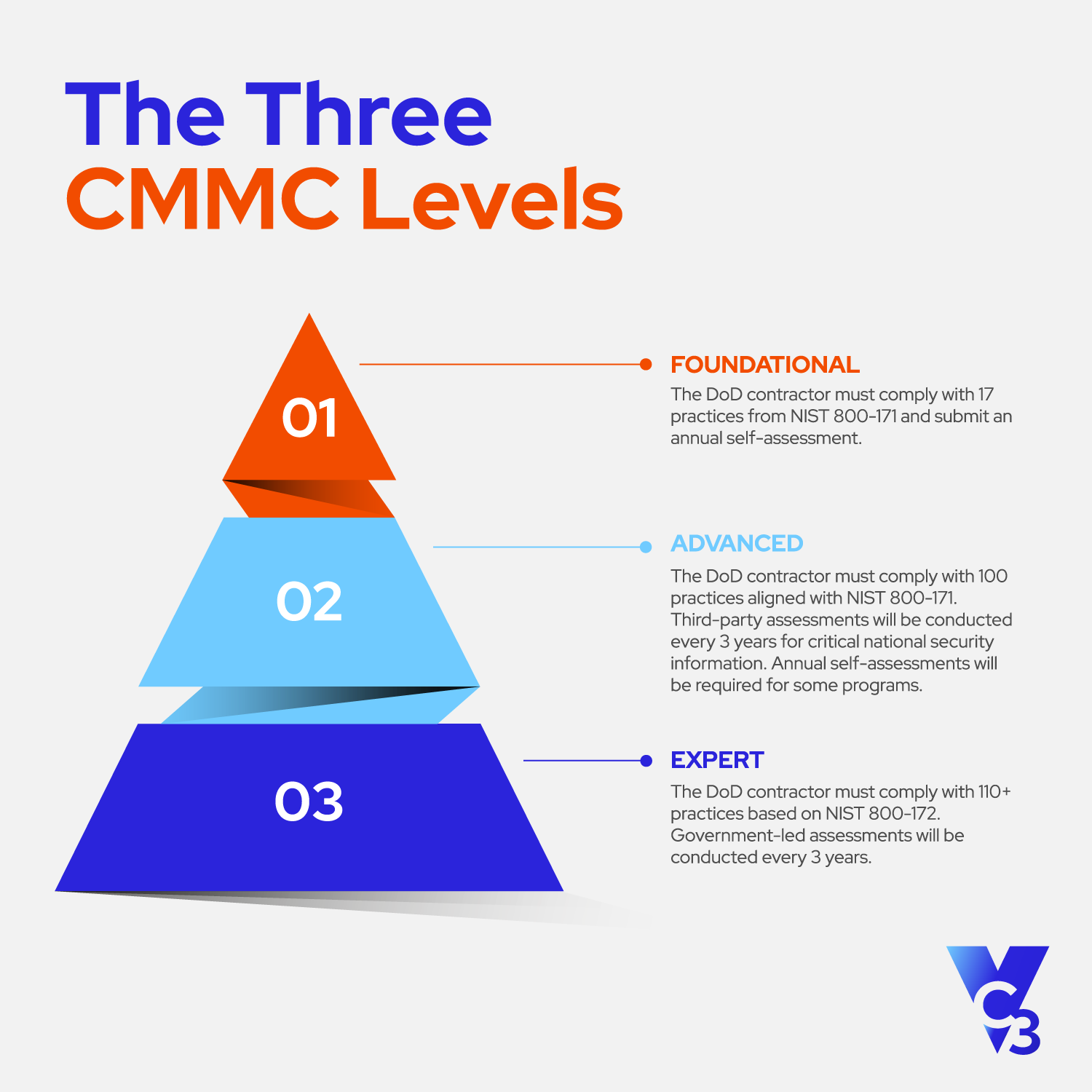
Level 1 (Foundational):
- Focus - Basic safeguarding of FCI
- Requirements - 15 basic cybersecurity practices
- Assessment - Annual self-assessment
Level 2 (Advanced): Most contractors need to meet these standards.
- Focus - Protection of CUI
- Requirements - 110 security practices aligned with NIST SP 800-171
- Assessment - Triennial third-party assessment for most contractors (with some lower risk contracts allowing self-assessment)
Level 3 (Expert):
- Focus - Protection of critical CUI with a higher potential impact on national security and defense than Level 2
- Requirements - Same as Level 2 plus an additional 24 practices from NIST SP 800-172
- Assessment - Government-led assessments every three years
CMMC Gap Assessment, Deliverables, and Continuous Compliance
With such strict CMMC compliance requirements, it’s a bit unfair to dump a gap assessment in your lap and walk away.
Instead, VC3 offers a continuous compliance approach so that you’re solving your compliance, security, and IT problems in a long-term, holistic fashion.
To help, VC3:
- Meets your business where you are on your unique compliance journey.
- Centralizes compliance accountability.
- Simplifies your current operational, IT, and security environments.
- Provides continuous management to ensure ongoing compliance.
- Provides the expertise required to navigate complex regulatory compliance.
Gap Assessment Process
Our gap assessment allows us to paint a holistic picture of your current compliance posture. This step of the process requires a significant amount of collaboration with your staff—including a review of your non-technical as well as your technical security policies. This means that HR and department heads will need to be involved.
We’ll guide you through a process that has five steps.
-
Step 1: Initial Consultation and Data Collection
During our initial conversations and while we collect some data about your environment, we will focus on a few areas:
• Understanding your Controlled Unclassified Information (CUI) data flow: CUI refers to sensitive government data that, while not classified, requires protection from unauthorized access and distribution. We will analyze the flow of your CUI data—where it originates and how it’s processed, stored, transmitted, accessed, and used.
• Collecting and reviewing your existing cybersecurity policies, procedures, and documentation: This helps us look for noncompliance gaps and learn more about your cybersecurity environment.
• Assessing your security architecture, technologies in use, and any existing compliance reports or audits: We will learn more about your cybersecurity strategy, tools, and compliance history. -
Step 2: Interviews with Key Personnel
While we can do much of the technical portion of the assessment on our own, this process is highly interactive and requires significant time spent with you to discuss the controls and what’s needed to meet them.
• Interviews: We will conduct structured interviews with your IT staff, security officers, executive management, and other relevant stakeholders.
• Discussions: We will seek to understand perceived versus actual security needs, concerns, and expectations from various departments.
• Qualitative Data: We will gather qualitative data about your security culture, employee security awareness, and stakeholder engagement in cybersecurity initiatives. -
Step 3: Technical and Process Evaluation
Next, we’ll take all the information learned, evaluate your environment, and begin to build a picture of your current state.
• Evaluation: We will evaluate the effectiveness and coverage of your current cybersecurity measures against the CMMC Level 2 categories and subcategories.
• Assessment: We will assess your integration of cybersecurity practices into your daily operations and decision-making processes.
• Gaps: We will identify strengths, weaknesses, and potential areas for improvement within the CMMC cybersecurity framework. -
Step 4: Gap Analysis Execution
Compliance requirements can be difficult to interpret. We’ll walk you through a detailed analysis of your current alignment for the level of compliance you need and provide recommendations for what is needed to pass your third-party audit.
• Checklist: We will utilize a detailed checklist aligned with CMMC Level 2 standards to methodically identify areas of non-compliance.
• Gap Analysis: We will analyze compliance gaps to determine underlying causes, potential risks, and any impact on your security posture.
• Recommendations: We will develop a prioritized list of recommendations for addressing any identified gaps, taking into consideration your business objectives, resources, and risk tolerance. -
Step 5: Gap Assessment Deliverables
With the results of your Gap Analysis in hand, your next step is to plan how you’re going to implement the missing security controls. These controls will include both technical and non-technical measures. That means that you’ll need to involve multiple departments, not just IT. And, of course, VC3 will help with the following deliverables.
• System Security Plan (SSP): An SSP is a report that outlines the discrepancies between your current security controls and the CMMC Level 2 requirements.
• Plan of Actions & Milestones (POA&M): A POA&M is an actionable plan that prioritizes what identified gaps to address, giving you a roadmap to achieve full compliance with the CMMC Level 2 requirements.
• Supplier Performance Risk System (SPRS) Score: Subcontractors are required to update their SPRS score so primary contractors can see it.
There’s no one-size-fits-all solution for how to achieve CMMC compliance. In fact, there may be numerous options that will meet regulations. In addition to providing you with the information you need to make decisions about how you’ll meet CMMC regulations, we can bring you other recommendations that will allow you to reduce the scope of compliance and reduce the costs of your audit.
Ongoing Cybersecurity Management
Once you achieve CMMC compliance, the controls that you put in place need to be managed. Even with an internal IT team, many organizations are outsourcing compliance because it’s the most efficient way to make sure you have all the knowledge, skills, and tools needed to maintain CMMC compliance without interruption.
To help you stay continuously compliant, VC3:
- Enacts Your POA&M: After developing a customized strategy for bridging any identified gaps during the gap analysis, we will enact this actionable roadmap in a practical, phased way, addressing immediate compliance needs while also outlining a trajectory for long-term security improvements. The plan will act as a guide for achieving and upholding ongoing compliance.
- Creates Policies and Procedures: By leveraging the gap analysis findings and roadmap stages, VC3 will collaborate with you to formulate tailored policies and procedures that align with any applicable security controls. These documents will establish clear, actionable guidelines for maintaining compliance and best practices as part of your daily operations.
- Continuously Monitors and Reports: VC3 will continuously monitor the SSP—involving systematic evaluations of security controls to proactively identify and mitigate non-compliant controls—to help you stay current with evolving cybersecurity trends and applicable requirements.
How VC3 Can Help Your Organization Prepare For CMMC Compliance
Although it may seem daunting, Cybersecurity Maturity Model Certification (CMMC) does not have to be a strenuous process.
As a CMMC Registered Provider Organization (RPO), we help organizations implement and maintain the controls of CMMC so they can bid on contracts with the Department of Defense and its supply chain. With over 30 years of experience helping companies with compliance requirements, you can expect to be promptly prepared for any CMMC certification level as quickly and painlessly as possible.
The DoD recognizes that security is an utmost concern, and should never be substituted for cost, schedule, or performance. The Department is committed to keeping sensitive data safe and protecting all parties involved in the contract process.
We are committed to getting organizations certified, quickly and efficiently.

VC3 keeps your organization protected and prepared.
1,100+ municipalities and 700+ businesses turn to VC3 to get out of the IT trenches and back to working on what matters.
of Experience Evolving with the Threat Landscape
Average Relationship Tenure
98% of Employees Are Technical
The capacity, skill set, and experience to help you AIM higher.
-
Comprehensive compliance solutions
Our comprehensive compliance solutions are tailored to meet your organization’s unique needs, ensuring seamless adherence to CMMC guidelines. From initial assessment to ongoing monitoring, we provide end-to-end services that simplify the compliance process and fortify your cybersecurity defenses.
-
Guidance and support from a vCISO and CMMC Registered Practitioners
Expert guidance from a vCISO and CMMC Registered Practitioners ensures your organization meets and exceeds CMMC requirements. Our specialists bring a wealth of experience and knowledge to your organization, offering tailored strategies and continuous support to help you navigate the complexities of cybersecurity compliance.
-
FedRAMP compliant
Ensuring the highest level of security with FedRAMP compliance, our solutions meet stringent federal standards to protect your sensitive data. By helping you adhere to these rigorous requirements, you minimize risk and enhance your organization's cybersecurity posture.
-
Proven cybersecurity and compliance track record
With a proven track record in cybersecurity and compliance, VC3 safeguards your operations and ensures compliance with CMMC standards. Our history of successful implementations and satisfied clients speaks to our ability to protect your critical assets and maintain the integrity of your data.
Our approach to technology enables your organization to AIM Higher.
Lots of companies can set up your laptops or manage your infrastructure. In order to contend with today's challenges, you need more than a break-fix vendor with a "24/7" helpdesk ticket to nowhere. You need a proactive partner that stops the issues before they start. That's where VC3 comes in.
Let's talk about how VC3 can help you AIM higher.
Cybersecurity Resources + Insights
CMMC 2.0 Compliance Explained

3 Most Common Advanced Technologies Businesses Need For Their CMMC Remediat...
