Filter by

Blog
|
8 min read
Healthy Compliance: Strengthening Your Healthcare IT Infrastructure to Meet...
Get a full break down of the essential elements of an IT strategy that aligns with HIPAA’s technical safeguards that is ...
Read More

Blog
|
3 Min Read
Is Your Municipality Compliant with CJIS’s Updated MFA Security Policy?
This new CJIS MFA mandate enhances security by ensuring that only authorized personnel can access sensitive law enforcem...
Read More

Blog
|
4 Min Read
CMMC Final Rule Signals Compliance Ramp Up
After five years and several iterations, the Department of Defense (DoD) has released its final version of Cybersecurity...
Read More
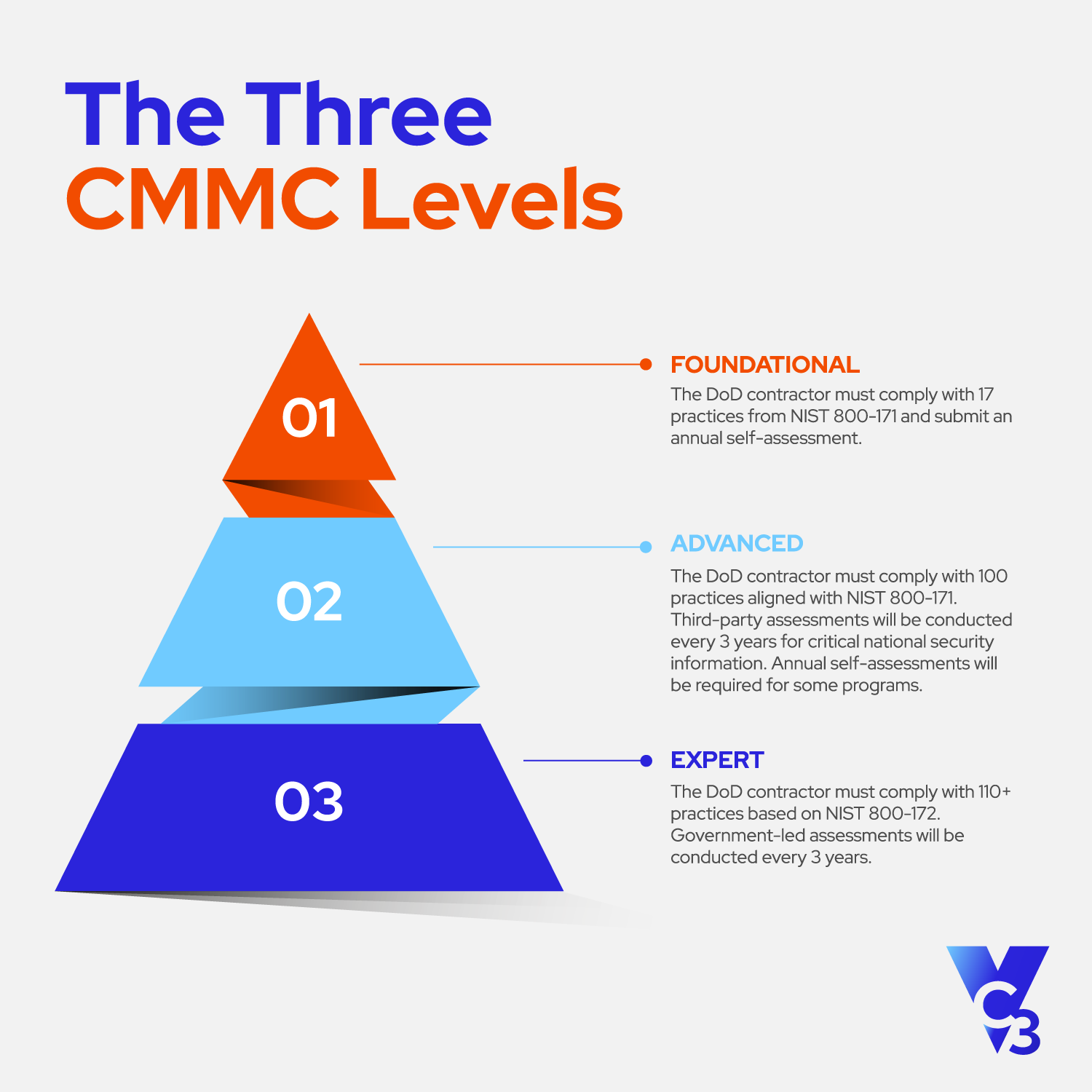
Guides
|
CMMC 2.0 Compliance Explained
Learn how the DoD supply chain will communicate and verify cyber security stature, what CMMC 2.0 means for Southern Cali...
Read More

Blog
|
5 Min Read
How Poor Network Infrastructure Jeopardizes Patients at Elderly Care Organi...
Elderly care facilities face a unique set of challenges when it comes to information technology. IT support problems in ...
Read More

Blog
|
5 Min Read
Before Busy Season: What CPA Firms Need to Do Now to Ensure FTC Compliance
Before busy season overwhelms your firm, now is the time to make sure you’ve got your cybersecurity in shape by reviewin...
Read More
