Picture these cyber security scenarios – an infestation of adware-laced browsers was being installed across a business’s network but was rapidly spotted and removed. A user on their honeymoon logged into their work account from another country, but their account was quickly locked to avoid any malicious login attempts. A firewall with insufficient resources started randomly taking the network down but was swiftly diagnosed and corrected.
These are all real examples of how a Security Information and Event Management (SIEM) system helps protect businesses.
A lot goes into an effective cyber security strategy, and keeping track of all of it all can be challenging. The best way to monitor all those different security tools (which give you with an overall picture of your cyber security posture) is with SIEM.
In this article, we'll explore:
Let’s dive in.
What Is Security Information and Event Management (SIEM)?
SIEM (pronounced sim) is a system that compiles and assesses cyber security-related log entries to identify any signs of malicious or prohibited activity on your network. This enables businesses to determine the nature and source of attacks more rapidly than they could without it.
When it comes to cyber incidents, seconds matter.
The primary function of a SIEM system is to aggregate and correlate data from multiple sources, including firewalls, intrusion detection systems, servers, workstations, and endpoint detection and response (EDR) systems.
When a SIEM system identifies something out of the ordinary, it logs the information and generates an alert for your cyber security team. It may also be tied into other security controls to stop the progress of specific activities.
With SIEM, businesses can get a clear picture of their security posture, improve their risk profile, and protect their data from potential threats.
How Does SIEM Work?
SIEM gathers event and log data created by applications, host systems, and security devices throughout a business’s infrastructure, all in one place. It identifies, sorts, and categorizes data into successful logins, malware activity, and other likely malicious activity and security threats.
It includes event correlation, incident response management, threat intelligence, and breach detection. It also monitors internal and external network activity, providing data analytics that helps businesses understand their security posture. And thanks to the power of machine learning and artificial intelligence (AI), SIEM also provides advanced user and identity behavior analytics (UEBA).
%20works-Jul-14-2023-02-49-18-8027-AM.png?width=600&name=how%20security%20information%20and%20event%20management%20(SIEM)%20works-Jul-14-2023-02-49-18-8027-AM.png)
Since SIEM has a comprehensive view of network activity and cloud integrations, it can also identify and alert on suspicious absences of activity in your environment, which can indicate service failures or misconfigurations.
It generates alerts when potential security, compliance, or performance problems are identified. Businesses can categorize the alerts as high or low priority with a predefined set of rules.
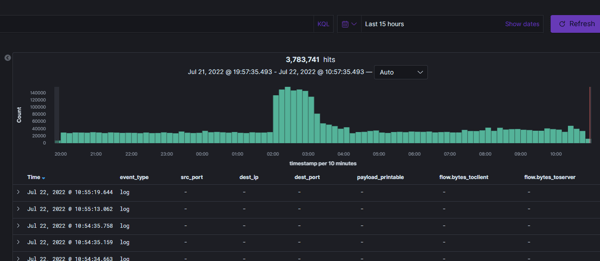 A SIEM system can aggregate log information from many sources, which can be queried to find anomalies and determine trends.
A SIEM system can aggregate log information from many sources, which can be queried to find anomalies and determine trends.
For example, an account that generates 20 failed login attempts in a 20-minute duration would be considered suspicious but categorized as low-priority. That’s because it’s possible the login attempts were made by a user who couldn’t remember their password (we've all been there 🤦♂️).
However, a user account with 200 failed attempts in 20 minutes would get flagged as a high-priority incident because there’s a good chance it's a brute-force attack in progress, or a misconfigured application that's causing account lockouts and failed service.
SIEM software generally includes these features:
- Data aggregation from a variety of sources.
- Data analysis to look for patterns that could indicate a security threat.
- Reporting and alerting to help businesses identify and respond to potential threats.
- Integration with other security tools, such as firewalls and intrusion detection systems.
Why Should Your Business Use SIEM?
One of the main reasons organizations use SIEM is because it's nearly impossible to effectively manually monitor the vast amount of data that cyber security tools generate. A SIEM system filters through all the data and prioritize alerts, making security more manageable.
And given that log management is at the core of SIEM, as more logs from cyber security sources get fed into the SIEM system, the more it generates actionable reports. This feature enables SIEM to compare relevant events by cross-referencing logs from multiple sources.
1. Detect Incidents You May Not Have Known About Otherwise
SIEM solutions allow businesses to detect threats that may otherwise go undetected.
For example, SIEM analyzes log entries to identify signs of malicious activities. It gathers events from multiple sources across a network and recreates the timeline of an attack. This feature enables businesses to determine the nature of an attack.
Otherwise, the events might go unnoticed.
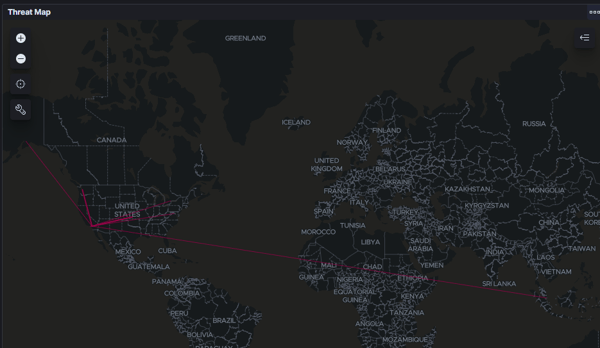 SIEM can enrich the information in its reports, such as adding geolocation data, which helps determine the next steps in securing your network.
SIEM can enrich the information in its reports, such as adding geolocation data, which helps determine the next steps in securing your network.
2. Respond to Security Incidents More Effectively
SIEM makes it easier and faster for your team to identify and react to potential threats by centralizing your cyber security data.
A SIEM system enhances cyber incident management by:
- Uncovering the route an attack takes across the network.
- Identifying compromised sources.
- Providing automation to stop attacks in progress.
3. Improve Your Security Posture
SIEM provides a single pane of glass for security data from across the IT environment and analyzes it for signs of threats. This visibility into all network activity helps identify potential vulnerabilities and risks and take steps to remedy them before they’re exploited.
4. Meet Compliance Regulations or Insurance Requirements
Since a SIEM system generates reports on all the logged security events, it can help organizations meet compliance requirements like CMMC and NIST. Without SIEM, organizations would have to collect log data and manually compile reports. This can be a difficult (if not impossible) task.
Requirements for cyber liability insurance are increasing. While SIEM isn't a common requirement yet in most industries, having it in place will help you get better rates since you're doing more to prevent a loss.
5. Increase Efficiency, Save Time and Money
SIEM helps reduce the time it takes to investigate and resolve incidents since all the relevant information is available in one place. SIEM also automates routine tasks, such as log collection and correlation, which reduces the workload of cyber security teams.
Ready to Get Started with SIEM?
A SIEM solution is one of the most effective ways of preventing cyber security incidents, detecting threats in real-time, and complying with regulations. By selecting the right vendor and following best practices, you can ensure a seamless SIEM implementation for your business.
If you need help with SIEM or your overall cyber security strategy, reach out to us today. VC3 isn’t just an MSP; we’re also an MSSP with a proven track record of helping businesses improve their cyber security posture.


