While a spam email may occasionally trick your city employees, it’s safe to say that normal spam emails are full of red flags. The writing is terrible, the email address looks obviously wrong, or the information requested from you is bizarre. Immediately, you flag that email as spam because you’ve seen through the amateurish scam.
But because cities are big targets for cybercriminals, you might occasionally become the subject of a sophisticated, targeted email scam—so sophisticated that it’s really, really hard to know if the email is spam.
If you don’t believe this situation could happen to you, meet Stephanie Settles, City Clerk and Treasurer of Paris, Kentucky—a city with a population of a little under 10,000 and a staff size of 125. In other words, it happened to a city that’s probably around your size.
After sharing her story at a recent cybersecurity presentation, about a fourth to a third of the room said they had received similar emails. In this interview, Settles talks to us about what happened, how she ended up detecting the complex spoof email, and how cities can stay vigilant against similar attacks.
So, you received a spoof email but didn’t know it was a spoof at first. Talk about what happened.
I received an email from my “City Manager.” You’ll soon see why I put that title in quotes. Coincidentally, the real City Manager left my office 15 minutes prior to me receiving the first email from “him.”
My City Manager was leaving town for a training session and we were making sure things had been processed and paid before he left. I had told him I was going across the street to pick up a sandwich for lunch and would be right back, and that if he needed or forgot something to let me know.
After I returned with my sandwich and sat at my desk, I received this email.
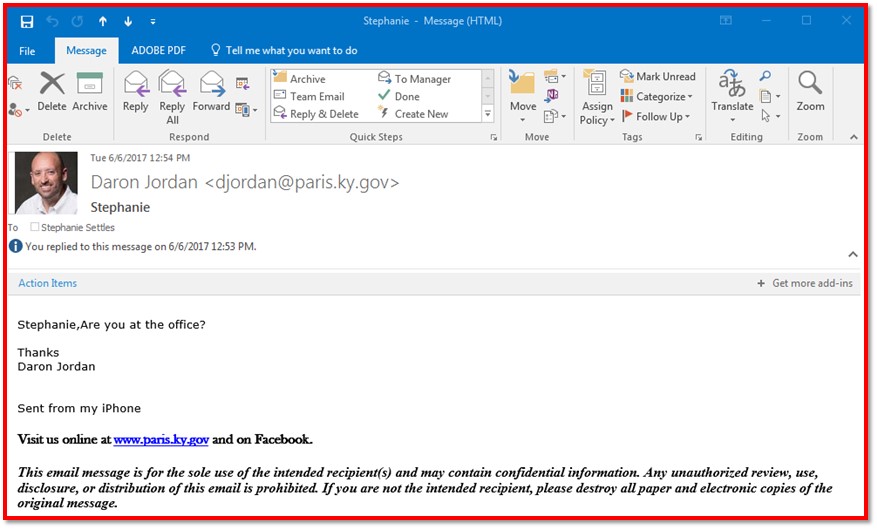
I was thinking, “Oh, he must have forgotten something.” Remember, I was helping him process paperwork and payments before he left. The timing of this message made total sense. So, I responded to the email. Nothing seemed abnormal at this point.
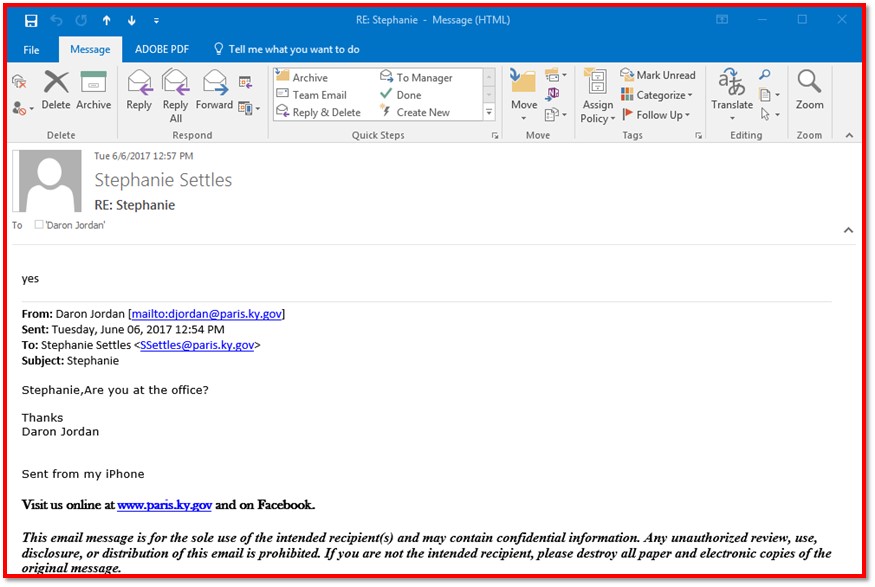
Then I received the following email from “him.”
Again, if I looked at this quickly, the message still seemed legitimate. The real City Manager always addresses us by our first names. It would not be unusual for him to request a transfer considering we were paying bills that day. So, I responded back.
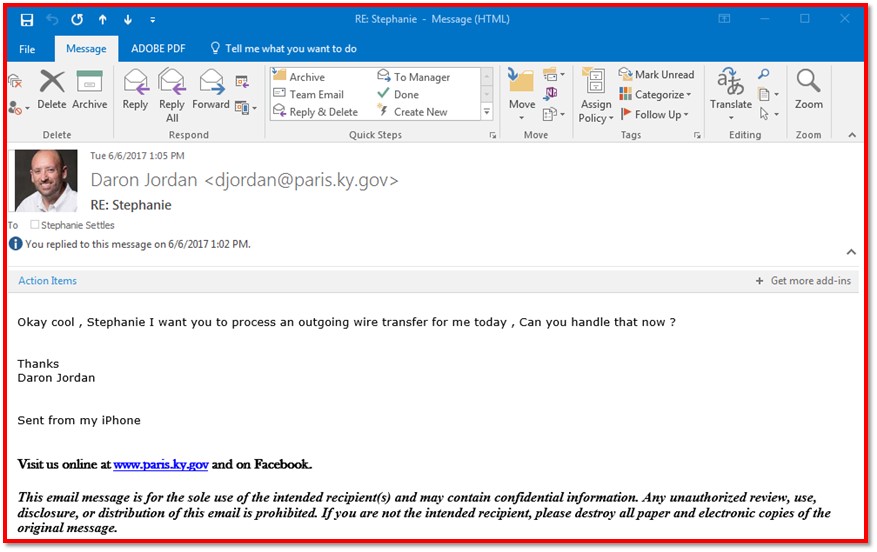
When “he” sent the following email, the red flags started.
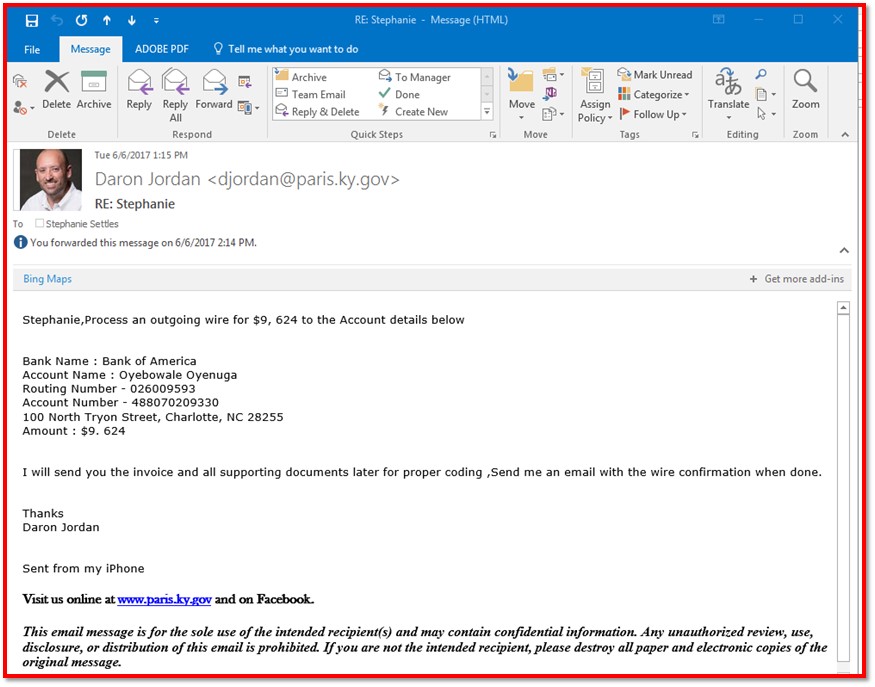
At this point, I noticed that the account name looked suspicious and the dollar amount seemed iffy. At our City, multiple signatures are required to spend over $9,000. But the language still sounded like my City Manager—especially the part about sending me an invoice and supporting documents for proper coding. He uses that language in his emails.
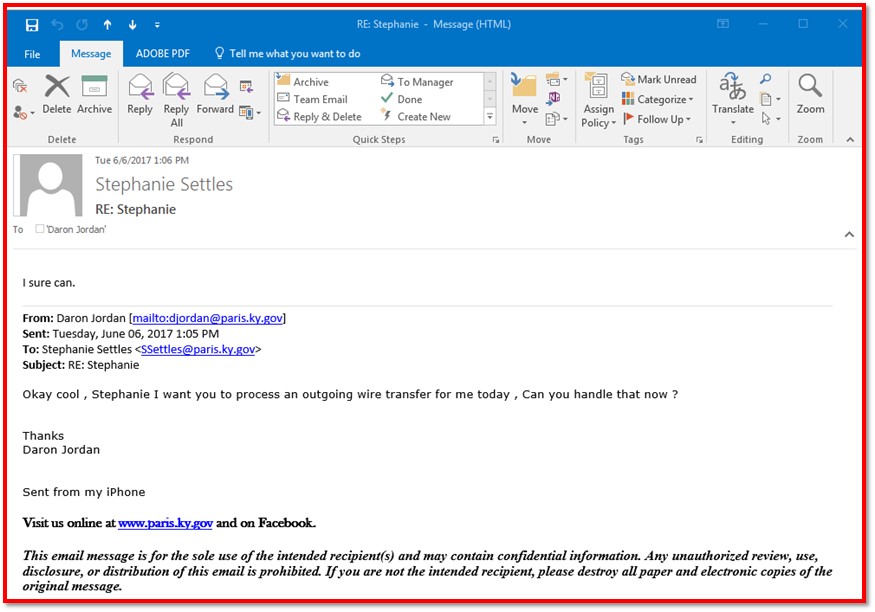
However, I was ready to tell him that I could not complete this request without proper approvals. It’s when I began to respond to this email that I 100% knew it was a spoof. Look at the email address for the “city manager.”
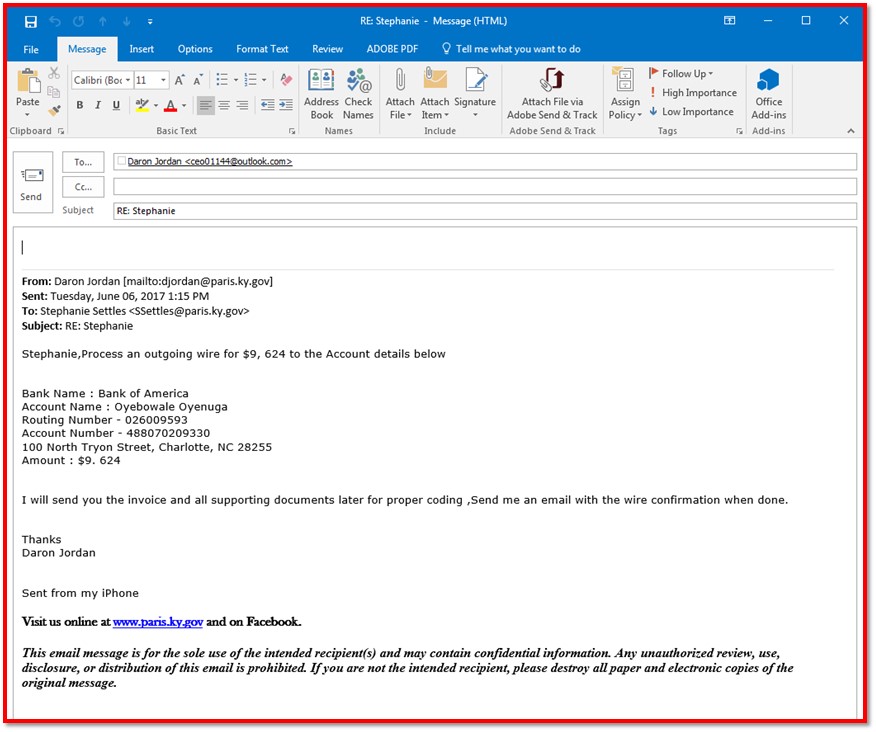
The email address—with the “ceo01144” name—clearly did not match our City Manager’s email address. Then, I made some comparisons with a normal email from him.
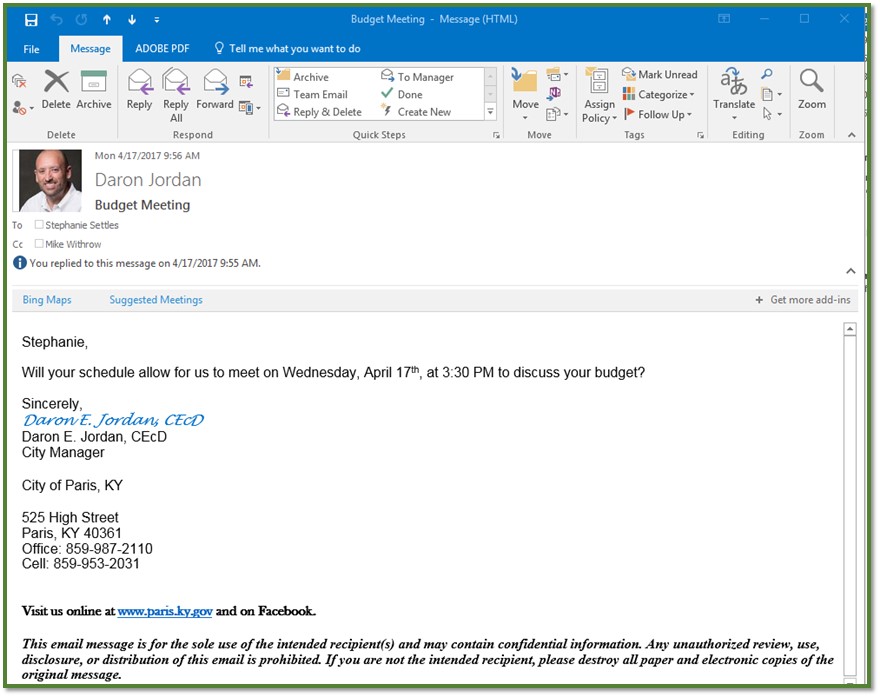
In a normal email, my City Manager typically does not reply to emails from his cell phone. Typically, he logs into his computer and replies to emails. Now, I know that if I see something from him that says “sent from my iPhone” that it is a spoof email.
What made this spoof email so tricky to spot?
Most importantly, the timing, language, and request made it seem like a normal email. Some secondary factors also made it tricky to detect that it was a spam email:
- The emails contained a photo of the real City Manager.
- The top of the emails referenced the correct email address.
- The real City Manager always begins his emails with the person’s name he is addressing.
- The City’s email disclaimer was at the bottom of the emails.
- The emails came into my inbox grouped into the same “real” inbox for our paris.ky.gov email domain instead of appearing in my inbox from a new email address.
- Each email that the “City Manager” used to reply to me was a new email. In other words, each time he responded to me, he began an entirely new email thread. Normally, a discussion like this would just form one long email thread as we responded to each other.
Why is this kind of an email a security concern?
Let’s say that I couldn’t detect that this email was spam. Then, a criminal could have obtained access to the city’s bank accounts or other sensitive and personal information. That kind of information in the wrong hands has the potential to cripple a city and interfere with our servers and processing systems, harming our data integrity.
Plus, cities can be vulnerable because we’re often so busy and distracted. For example, I was so busy that day that I decided to take a working lunch at my desk. I spotted the red flags, but imagine someone less experienced or more distracted than me. It shows, with one slip, how easy a spammer can trick someone if they’re not paying attention.
What are some ways that cities can prevent against this kind of email spoofing attack?
This seemed extremely targeted, malicious, and criminal. For someone to go to the extent of retrieving someone’s photo, spoofing an email address, imitating the person’s language, and targeting me with a request that’s not terribly unusual means that’s it’s all but identity theft.
Even with such a sophisticated attack, there are many ways that cities can prevent a spammer from gaining access to your sensitive information by following a few tips:
- Change your passwords frequently.
- Run full virus scans on a frequent basis.
- Take notice of the email address when you respond to someone.
- If in doubt of an email, just pick up the phone and call the person. It’s better to be safe than sorry.
On top of that, we consider IT in a Box as an extra layer of security—our security blanket, if you will—to help protect our data. They keep antivirus and antispam software running and up to date, software patched and updated, and our hardware secured. They also help make sure that our employees are educated about spotting phishing emails, not clicking on malicious links or attachments, not sharing sensitive or confidential information with an untrusted person, and knowing who to call when something like this happens.
Concerned about your readiness in the face of a sophisticated spoof email? Reach out to us today.
Original Date: 9/6/2017





