Cybersecurity sounds like something that falls under the responsibility of the IT department. IT may handle many of the responsibilities that go along with protecting your company from cyber threats, but that doesn’t make security the sole responsibility of the IT department.
Ensuring that your business doesn’t fall prey to a cyberattack is everyone’s responsibility.
With 43% of cyber attacks targeting small businesses, it’s more important than ever that everyone on your team participate in your cybersecurity measures.
Let’s take a look at 3 critical things to share with your employees that will help keep your business safe:
- Every end-user must be on the lookout for scams
- Watch what you click!
- Familiarize yourself with the steps the IT team takes to protect you
1. Every end-user must be on the lookout for scams
Phishing scams attempt to gain private data through phone calls or emails, including passwords, financial information, or information about your clients. To avoid falling prey to a scam, make sure that you’re following these key steps.
Check email addresses carefully (and follow up separately if it seems odd)
Check email addresses carefully. Look closely to make sure Os haven’t been replaced with zeros, or the domain name hasn’t been changed from apple.com to applestore.com, for example.
If you receive a request from an unknown or suspicious address, follow up in person or by phone with the appropriate person.
Many scammers will also attempt to replicate an email that looks like it comes from a contact within your organization. Others will send you an email that appears to come from a trusted source, including vendors, like the example below that appears to be from Wells Fargo.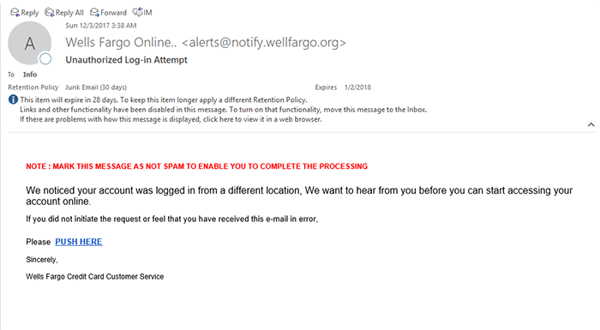
Example: Missing letters and misspelled words in an email address are clear signs of a phishing attempt.
It’s easy for scammers to spoof an email address to make it look like it’s from someone you’d be expecting an email from. So, if you get a request that’s out of the ordinary, question it. It’s better to err on the side of caution.
Pay attention to fake attachments
Always check attachments on emails carefully, especially before downloading. If you aren’t expecting an attachment from a specific source, don’t open or download it unless you can verify its legitimacy.
Never open an attachment that doesn’t come from a reputable source.
If you use Microsoft Office, you may want to view attachments in protected view before downloading them, especially if they originate from an unfamiliar source.

Be suspicious of out-of-the-ordinary payment instructions
Any time you get an odd request or payment instructions that don't seem right, follow up within your department before giving away any private or sensitive information. If you don't typically handle payments for your organization or you haven't made a recent request, keep in mind that there's no reason for anyone to send you a payment request.
Even if you handle payments regularly, ensure that they come from the right individual and follow the usual processes and instructions. If something seems off, you should always follow up with the company.
Be on the lookout for odd requests
If you receive a request for something out of the ordinary, don’t answer immediately. Instead, talk to someone who can tell you where the request originated and whether you should follow up on it.
That includes requests for information that you do not typically provide about your clients or information about your business that isn’t usually shared.
Pay attention to phone requests, too
Phone requests may appear to come from someone within the organization, but in some cases, they may originate from a scammer. Always confirm that you are speaking to the person they claim to be before providing any information about your clients, passwords, or organization.
Many scammers, for example, will call in pretending to be a member of your IT department, asking you to “log in” to a different location, where they will then gather your password for future use. If needed, call your IT team directly to confirm any requests.
Be aware -- some scammers may attempt to get personal information from you over the phone, specifically through what seems like small talk, in an effort to crack your passwords or gain access to your systems.
2. Watch what you click!
Clicking on the wrong link can cause a cascade of trouble for your business. Pay careful attention to what you’re clicking! Always confirm that the link goes where you expect.
Type addresses directly into the address bar rather than clicking on email links when possible. This simple strategy can help protect both your business and your personal information.
Avoid clicking on pop-ups since these can contain links to viruses.

3. Familiarize yourself with the steps the IT team takes to protect you
The IT team takes many steps to protect your business and decrease the impact of cyber attacks. As an employee of that business, you don’t have to understand every detail of cybersecurity, but you should have a decent idea of what protections the company has put in place and how to stay in line with those requirements.
Endpoint detection and response (EDR)
EDR software provides a vital layer of protection against many pieces of malware.
Familiarize yourself with the EDR software used by your organization – and what software isn’t used by your organization. Many organizations still use antivirus software, which is no longer sufficient to protect you from most cyberattacks. EDR uses machine learning to not only help you prevent but also detect attacks by identifying suspicious behavior and activities that signify a likely threat.
Managed firewalls
Managed firewalls keep an eye on all traffic moving through your network. With a managed firewall, your team understands what traffic through your organization should look like, which means it can more easily flag any suspicious traffic.
Advanced threat protection
Either software or managed services can help catch more sophisticated cyber attacks, providing an additional layer of protection for your business. Advanced threat protection tools such as EDR, internal and external vulnerability scanning, and penetration testing help protect in the fight against cyber crime.
Good backups
If your business is hit by ransomware, locking you out of vital systems and away from critical information, or you get hit by malware that deletes your data, having good backups can make a huge difference in your business’s functionality.
Every employee should have a basic understanding of how those backups work. This includes how or when to access data if an incident occurs or something gets deleted unexpectedly.
Cybersecurity Services For Your US and Canada based Business
Among the many protections to your company, a managed security services provider can improve your overall security and provide a layer of protection against potential attacks.
Need a security assessment to get a better idea of how well your business is protected? Contact us today to learn more.
Editor’s Note: This article was originally published in December 2019. It has been revamped and updated with the latest information.





