Imagine that you’re an army out on the battlefield. As you face the enemy, your commander says, “Let’s go get ‘em!” Instead of moving together as a cohesive unit, everyone does whatever they can think of in the moment. The chaos you’re envisioning in this scene is due to a lack of strategy, planning, and practice.
That's exactly what it’s going to be like at your organization if you have to deal with a cyber attack without an Incident Response Plan.
A Cyber Incident Response Plan is part of NIST 800-171 security requirements and therefore part of Cybersecurity Maturity Model Certification (CMMC). However, all companies, not just those who need to follow regulatory compliance, need to have a documented plan that details how your people are going to act in the event of a security event.
Creating an Incident Response Plan allows you to think through what you need to do, make decisions and establish procedures ahead of time, and train everyone on the plan before an incident occurs.
Trying to figure everything out while you’re in the middle of the event is going to be very difficult. Everything will take longer, and you may not know what to do when the questions start coming at you in rapid-fire.
People will be asking you questions like:
- What are the steps that IT should take?
- Should we shut down our whole network or just part of it?
- What do we still have access to?
- How are we going to communicate if we can’t use our email?
- Who needs to be notified and who’s going to act as our main Point of Contact?
- Where are our backups and passwords?
- What (if anything) should we tell our customers?
- What do we need to do to re-establish minimum operations?
- Do we need to contact local law enforcement or the FBI?
- Who’s going to make the big business-impacting decisions?
The Incident Response Plan Process
When you create an Incident Response Plan, you’re actually creating a six-phase process that begins with preparation and ends with analyzing what happened so you can build up a stronger defense.
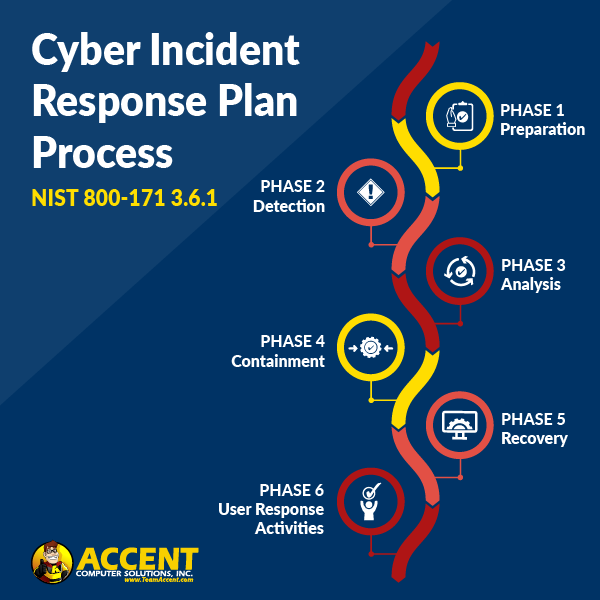
NIST 800-171 3.6.1 lists these phases as preparation, detection, analysis, containment, recovery, and user response activities.
This is followed by 3.6.2 requiring a process to document and report incidents, and 3.6.3, which requires organizations to regularly test and review their Incident Response processes.
Part of cyber incident training is to go through different threat scenarios that are the most likely to happen on that awful day when you have a cyber intruder. There are so many ways that an attack can take place that you can’t train for every potential situation, but training will jump-start thought processes and help your Incident Team to apply what they know and fill in the gaps as needed.
Roles and Responsibilities for Cyber Incident Response
If you don’t have a formal Incident Response Plan, then your plan is probably – “Call IT!”
While your IT team is going to be working the issue on the technical side, other people will be playing key roles both in preparation and implementation of your cyber incident response.
The more mature your plan, the more you’ll have these roles defined and their responsibilities documented, and the sooner you can address the potential business impact of the incident.
Two of the most important roles that come into play are Incident Manager and Communications Manager. Your lawyer and your insurance carrier may also be involved, depending on the severity of the incident.
Get Your Go-Bag Packed
A “Go-Bag” is an actual bag that contains hardware, software, cables, and other equipment that might be needed in a cyber incident response. It also contains paper copies of all the procedures and checklists included in your Incident Response Plan.
Having electronic copies is great, but you have to assume that your systems will be down in the event of a cyber incident. Old school paper copies will be your guide.
Prepare Now to Limit the Disruption
What will happen at your company when someone tells you there’s been a cyber incident? Is it going to be chaos? Or will you be able to say, “Let’s go get ‘em!” and your plan springs into action?
A cyber intrusion will cost you time and money, but the investment you make in being prepared to act will give you the best chance of minimizing damage to your business.
Uncover Security Holes with a Cyber Security Assessment
Not having an Incident Response Plan is a gap in your security strategy and can make you wonder what else you’re missing. Contact us to schedule a Cyber Risk and Security Assessment for an objective review and actionable recommendations.


