When you’re trying to understand what you’re supposed to do to follow Cybersecurity Maturity Model (CMMC) regulations, there’s a lot of information to digest. A lot.
Even with the new simplified 2.0 version of CMMC that the Department of Defense (DoD) released in November 2021, interpreting requirements and how exactly your company is going to meet them is still new territory for most executives and their IT managers.
Unless you want to make CMMC compliance your full-time job, it would be nice to have all that information boiled down so that you get to the point where you can act.
You must act because if you haven’t, you’re already late. Last year the DoD communicated with companies in their supply chain with a request to submit a CMMC System Security Plan by the end of 2020, yet many companies have not been able to do that.
Why? For many, it’s a lack of knowledge and training to interpret CMMC into action.
Whatever your reason, help is here. At VC3, we’ve not only taken the time to understand the intricacies of CMMC compliance but we’ve also been trained to help companies plan and do what they need to do to successfully attain and maintain compliance.
Here’s your boiled-down version of what the CMMC Self-Assessment is and what you need to do.
- The DoD Wants Your System Security Plan (SSP)
- What is a CMMC / NIST Gap Analysis?
- The CMMC Gap Analysis Process
- Submitting Your CMMC System Security Plan
- How a Registered Practitioner Can Help You Prepare for Your CMMC Self-Assessment
The DoD Wants Your System Security Plan (SSP)
Your System Security Plan (SSP) is what you’re going to submit to the DoD. Think of your SSP as the gathering place for all the information that you’re going to collect to communicate what you’re doing now to security Controlled Unclassified Information (CUI) and what you’re going to do to achieve full compliance.
If you’re just getting started with CMMC, you don’t have this document yet but you may have some of the pieces that go into it.
The SSP is comprised of:
- Names and contact info of company representatives
- Types of Controlled Unclassified Information (CUI) that you store and transmit
- Information about people who handle CUI
- Description of your network listing of all hardware and software
- Relationships with or connections to other systems.
- How security requirements in NIST 800-171 are implemented
Some of the info you’re going to gather – like lists of hardware and software. Some of the info you’re going to have to draft – like an up-to-date diagram of your network. You also should expect to do some investigation.
That’s where a Gap Analysis comes in.
What is a CMMC / NIST Gap Analysis?
A Gap Analysis is required to discover how closely you’re currently following security requirements detailed in NIST 800-171.
What is NIST 800-171?
This is the publication by the National Institute of Standards and Technology titled “Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations." In effect, these are the security rules that are the foundation of CMMC requirements.
NIST 800-171 includes 110 controls in 14 families or categories. A Gap Analysis will use the NIST 800-171 DoD Assessment Methodology and go through all of these to find out what you’re already doing that fulfills requirements, and where you’re lacking. For each control you have in place you get a score of “1” so your goal is 110.
It’s possible to get a negative score on your Gap Analysis if the controls that you’re lacking are the ones that are weighted. For example, you’ll get a +1 if you fulfill Basic Security Requirement 3.1.1, which is “Limit system access to authorized users, processes acting on behalf of authorized users, and devices (including other systems)” in place, but a -5 if you don’t.
It’s common for companies to receive a negative score on an initial Gap Analysis.
The CMMC Gap Analysis Process
CUI Scoping: Locating the Data
The first step in a Gap Analysis is to find out exactly where the Controlled Unclassified Information (CUI) is being stored. This can be very difficult to figure out if your customer didn’t identify the CUI in the first place. The only thing you can do is to start going back through the supply chain until you get to the link that has the CUI markings.
Identifying or scoping the location of the CUI is very important.
Not only do you need to know how controls are being applied to the data, knowing what you’re working with can help you isolate it in your network. A data flow diagram is helpful in these cases. This not only makes it easier to manage compliance, but it can save on costs when it comes time for your audit.
Documentation: System Diagrams and Control Verification
It’s not good enough to just say that you’re following a security control. You have to prove it. So an early step in drafting your SSP is going to be to gather documentation. This includes diagrams and descriptions of your network and connections. It also includes documentation for the evidence that you have practices and processes in place to support requirements in NIST 800-171.
If you’re working with a Registered Practitioner (RP), this will be a task that they facilitate. As they walk you through a Gap Analysis, RPs will help you gather documentation and give you recommendations for different ways that you can provide evidence for what you’re doing.
NIST Gap Analysis: Your Score on 110 Security Controls
The actual NIST gap analysis is made up of interviews, examinations, tests, and onsite walkthroughs. Whether you’re doing it yourself, or you’ve engaged with an RP to help walk you through it, this is the investigation that will uncover how close you are to that 110-score mentioned previously.
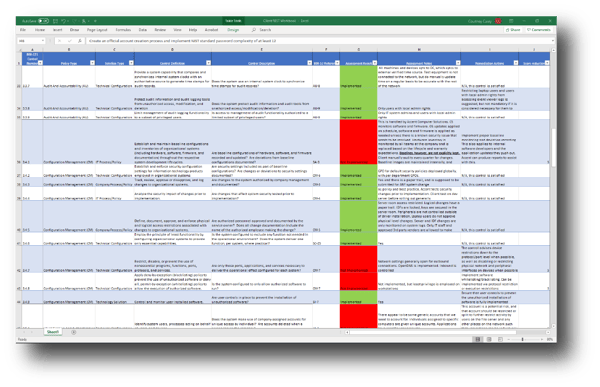 NIST Gap Analysis Discovery Example
NIST Gap Analysis Discovery Example
Keep in mind that NIST 800-171 is made up of both technical and non-technical controls. (If this is a surprise to you, you should read Cyber Security is a Shared Responsibility.) Your employee handbook may have some of the documentation you need, and your HR manager may need to be involved when it comes to employee training on security protocols.
Remediation Plan: How You’ll Close the Gaps
The findings that result from your audit will be the basis for your Remediation Plan or Plan of Action and Milestones (POAM). When you submit your Self-Assessment, you’ll have to detail exactly how you’re going to close any gaps in security and about how long it will take.
There’s no one-size-fits-all when it comes to following CMMC or NIST. There will likely be more than one way that you can meet a requirement. If you’re working with an RP, they’ll bring you recommendations that will help you to make good decisions for what’s attainable and manageable.
Submitting Your CMMC System Security Plan
When your System Security Plan is complete and you’ve gathered all of the documentation that goes with it, you’re ready to submit it to the DoD.
At this point, companies need a score and an estimated date that they plan to be compliant. However, some contractors are asking for more details from their subcontractors to show how far along they are on their journey to compliance.
How a Registered Practitioner Can Help You Prepare for Your CMMC Self-Assessment
The DoD knew that CMMC compliance would require expertise that manufacturers may not have internally, so they sanctioned the creation of Registered Provider Organizations (RPO) and the training of consultants, called Registered Practitioners (RP), to help.
VC3 is a CMMC RPO with 5 RP consultants on staff. Learn how we can help, or get in touch to talk to one of our CMMC consultants.
Note: This article was originally published in April 2021. It was updated in December 2021 to reflect CMMC 2.0 standards.





